TryHackMe Sudo Buffer Overflow-Writeup

Table Of Contents
3. Scanning
TryHackMe Sudo Buffer Overflow-Writeup
Sudo Buffer Overflow is a beginner level Linux machine on TryHackMe. The machine teaches us about vulnerabilities in sudo command. The machine is running sudo < 1.8.26 which is vulnerable to Buffer Overflow exploit if password feedback is turned on. In this machine, the password feedback is turned on so we exploit this Buffer Overflow to gain root access into the system
Connecting to HTB Vpn:
- First download the vpn file from the access page of tryhackme
2. Open the .ovpn file in your terminal with the following command
openvpn yourname.ovpn
3. Now as the “Initialization Completed” message appears on the screen you are connected to the hackthebox network
4. You can access the machine at the given ip
Scanning:
1. First let’s do a nmap scan on our target at 10.10.61.54
nmap -sV -A -p- 10.10.61.54
-sV : to get the service versions on each port
-A : to get information such as os details,traceroutes,ports etc
-p- : to scan all 65535 ports
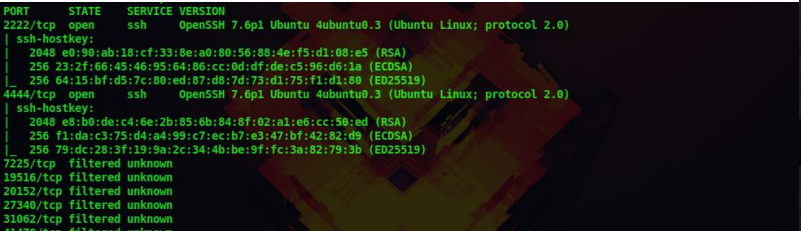
We get the following details from our scan
Certified Ethical Hacking
Gaining Access:
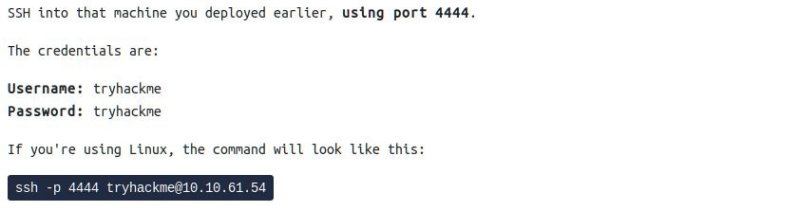
2. We are given the ssh credentials so lets log in
Privilege Escalation:
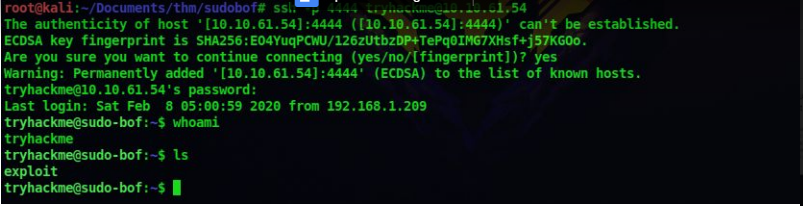
3. After logging in there is an executable file in the home directory
4. If we search for the sudo version we can see it is 1.8.21 and there is password feedback in the sudo command.

5. Since there is password feedback and the version is < 1.8.26 a buffer overflow exploit comes to my mind
https://www.linuxminion.com/sudo-stack-based-buffer-overflow-vulnerability- pwfeedback/
6. We have this exploit compiled and ready to exploit in our home folder.
So let’s run that to get a root shell
./exploit
Don’t forget to check out our latest Blogs – TryHackMe WgelCTF-Writeup




 TryHackMe Writeups
TryHackMe Writeups



